Industrial environments networks are often considered less secure than traditional IT environments. This is partly because OT systems were designed to operate autonomously with a focus on performance and real-time with less attention on security. Additionally, the equipment and communication protocols used in OT environments are often outdated and vulnerable to attacks.
The difficulty of updating equipment: Many industrial equipment are difficult to update due to their critical nature or very long lifecycle.
- The complexity of systems: Industrial systems are often complex and interconnected, making them difficult to manage and secure.
- Internal threats: Employees, subcontractors, or partners may access industrial systems and cause intentional or unintentional damage.
To enhance the security of industrial environments, it is important to have a secure-by-design approach, develop best practices of patching and coding and have the capability to monitor and respond when an incident occurs.
Security by design
Purdue model
The Purdue model was defined to establish best practices in terms of data separation between the OT and IT networks. Purdue Model is based on a hierarchical architecture, which divides the information system into six different levels. Each level represents a different aspect of the system and has its own unique set of security concerns and requirements. The six levels are:
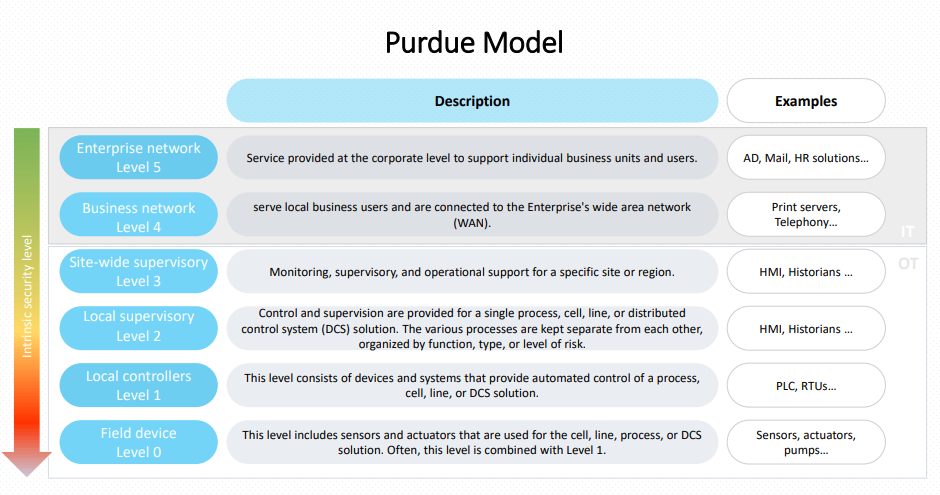
The Purdue model is a recognized standard in the management of OT infrastructures and proposes a security architecture based on network segmentation into different security zones, including the use of DMZ buffer zones, particularly between levels 3 and 4 where stand the industrial DMZ known as level 3.5. This allows for the protection of ICS and building automation and control systems (BACS) against external attacks and internal errors.
The Purdue model is a topic of debate among specialists regarding its relevance in current times, despite being an old model. One reason for this is its ability to support IoT where the boundaries between IT and OT are even more blurred. However, the Purdue model is a recognized standard in the management of OT infrastructures, and it is still a solid foundation that can be adapted based on industries specificities.
Segmentation
The segmentation of the OT network is an important security practice for companies that use operational technologies to control industrial equipment and processes. One of the reasons why OT network segmentation is important is to reduce the risk of attack propagation throughout the network. Hackers often attempt to penetrate OT networks to introduce malware or ransomware. If these attacks succeed in penetrating a system, they can quickly spread to other systems connected to the same network. Segmentation helps to limit the spread of these attacks and minimize damage.
There are two crucial points to bear in mind: First, it's crucial to keep all ICS protocols confined to the control network and never found them above level 3 of the Purdue model. Secondly, all low layers including the control level should never have direct internet access.
Hardening and patching
Hardening and patching are also important for the security of OT systems. However, this can be challenging because many OT systems use outdated operating systems that are no longer supported by vendors. This means that security patches are no longer available for these operating systems, making hardening and patching more difficult. Companies must find ways to harden and patch these systems or to reduce as much as possible the attack surfaces and the capacity of propagation if an attack occurs by implementing an effective segmentation.
In addition to hardening and patching, it is also important to follow good coding practices, and it’s even true for PLCs programmers. A guide of the 20 best practices for coding PLCs has been developed, based on the well-known OWASP Top 10 format, in order to create robust and secure PLC programs. The list of recommendations in detail can be found here.
Identification and Monitoring
Asset Identification
To protect against a cyber-attack, it is crucial to know your assets, and the ICS environment is no exception to this rule. The activity of asset identification must be assigned and updated regularly to ensure that all assets are identified and monitored. The identification of "crown jewels," that is, assets that, if they were to fail, would partially or completely interrupt the production line, is essential to isolate and provide necessary protection measures for these critical elements. Physical equipment, data flows, and networks must be inventoried.
Baseline
Defining a baseline is a key element for detecting incidents in the ICS environment because it allows for quickly detecting any anomalies, whether malicious or due to a configuration error, which in either case benefits these systems' availability criteria. Therefore, it is necessary to have a baseline of data and network flows, as well as essential configuration files for the industrial process. In the case of the Stuxnet attack, the attack ultimately succeeded because the attackers manipulated the Siemens controller project file. Having a baseline of these files would have prevented the attack.
Monitoring
Regarding network monitoring, it is essential to have a baseline of established protocols and communications between devices, as well as to identify all remote connections, including wireless/radio communications protocols.
It is still essential to be very careful in identifying ICS assets, many solutions exist, however solutions that use active network scans should be considered with cautious as it could disrupt the operation of some industrial equipments that are very sensitive to ICMP or other requests. In this case, it is safer to turn to passive monitoring solutions such as Nozomi, Claroty, or Microsoft Defender for IoT.
There are two crucial points to keep in mind when It comes to monitoring OT networks:
- Identifying remote connections (RDP, VPN, TeamViewer...) and ensuring that these connections are identified and secured: Interconnections with 3rd parties and trusted networks, suppliers, service providers, integrators…
- Elements that are on the border between IT and OT, such as the data historian, should require special attention.
Finally, it is necessary to retrieve the logs of all significant devices in the production process and send them to a SIEM to proactively detect and be able to respond as early as possible to an attack, especially when we know that ICS-oriented attacks are typically present on networks for several months or even years before the attack execution phase.
Incident response
In order to effectively respond to incidents in ICS environments, it is crucial to have a dedicated incident response team that is trained specifically for these environments. This team should have a deep understanding of the processes and systems in place, as well as the potential impact of any disruption or breach.
Moreover, it is important that this team has regular contact with the operational staff and other key stakeholders within the ICS environment, in order to stay up to date on any changes or updates to systems and processes. This can help ensure that the incident response team is able to respond quickly and effectively in the event of an incident, minimizing the potential impact on operations and minimizing downtime.
ICS cyber kill chain
Attacks targeting industrial control systems (ICS) are becoming increasingly common and sophisticated, with approaches and attack techniques specifically tailored for industrial targets.
The ICS Cyber Kill Chain is a model developed by the SANS Institute to help security professionals understand the stages of an ICS attack and implement effective prevention measures. This model consists of two main phases: the intrusion/learning phase and the attack phase.
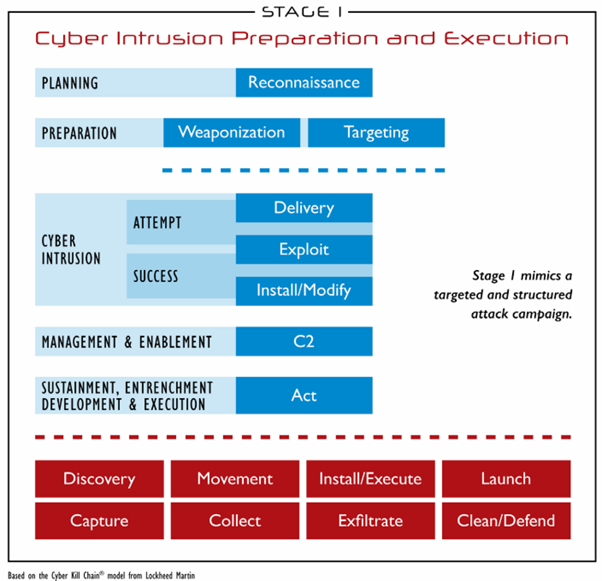
The first phase, the intrusion and learning phase, is crucial for attackers as it allows them to gather information about the ICS system and potential vulnerabilities. This phase includes several stages:
- Reconnaissance: Attackers conduct a thorough search on the target to identify potential vulnerabilities and entry points.
- Delivery: Attackers deploy malware onto the target system, usually via phishing or social engineering techniques.
- Exploitation: Attackers use identified vulnerabilities to penetrate the target system.
- Installation: Attackers install malware onto the ICS system to gain remote control.
The second phase, the actual attack phase, is triggered once attackers have successfully penetrated the ICS system. This phase also includes several key stages:
- Privilege escalation: Attackers attempt to gain elevated privileges on the system to access advanced features.
- Propagation: Attackers seek to extend their control over other ICS systems within the organization.
- Malicious act: Attackers use their access to the ICS system to carry out malicious acts such as parameter modifications, disruptions to industrial processes, or ransomware attacks.
Stuxnet and Havex are very good examples of attacks that illustrate the stages of the ICS cyber kill chain. Stuxnet attackers accomplished a remarkable achievement by traversing each zone of the Purdue model and ultimately reaching level 0, where the nuclear centrifuges were located. To accomplish this, the attack passed through all the stages of the ICS Cyber Kill Chain.
It is important to note that attacks targeting Industrial Control Systems (ICS) require a long duration of reconnaissance and learning of the targeted systems' technologies, as well as the development of specific payloads for ICS components. In fact, Stuxnet was detected in 2010, despite the attack campaign starting as far back as 2006, post-analysis of the attacks revealed that it could have been detected and stopped at an early stage if efficient detection capabilities had been deployed.
Havex is a RAT-type malware adapted to target ICS that has been used in espionage campaigns targeting industrial and energy companies. Different methods were used to introduce the malware to targets, including distribution via spear phishing with a malicious attachment, as well as through "watering hole" attacks by compromising websites frequented by industrial workers and inserting the malware or by providing ICS software containing malicious code that would infect computers upon downloading and installing. The goal of this attack campaign was not to disrupt but to steal sensitive information from its target for espionage purposes. This goal could be achieved without reaching level 2 of the ICS cyber kill chain model.
Security professionals seeking to protect industrial control systems against potential attacks must understand the ICS Cyber Kill Chain. By identifying and proactively protecting vulnerable areas at each stage of the attack chain, the risk of successful attacks on ICS systems can be significantly reduced.
There are some specific resources that could be helpful for ICS security analysts:
- SANS ICS Cyber Kill Chain model
- ICS MITRE attacks : Like the very know MITRE Attack framework, they developed a framework for the ICS environment taking into consideration the specificity of this environment
- Threat intelligence: CISA reports regularly about newly discovers vulnerabilities on ICS-specific components