Introduction
Cybersecurity is a never-ending race between attackers and defenders. As soon as a new vulnerability is disclosed, all involved parties are off to the races. While defenders look to quickly minimize the impact, attackers are keen to develop their exploits rapidly to start compromising their victims. The adversary’s acts are mostly motivated by either financial profit, political interest, or simply to gain reputation within the hacking community.
This article marks the first part of our series: “Unlocking true security potential by deploying a Security Operations Center (SOC)”. In this series we will present a comprehensive roadmap on deploying a SOC, starting with theoretical considerations, before outlining concrete solutions. This article will show; where in the risk management process a SOC can be positioned and what benefits it offers to an organization. In the end the reader should have a clear understanding of how running a SOC helps the risk management process of any organization. If you are interested in knowing more about the different deployment options of a SOC along
What is Cyber Risk Management?
Before we can start to introduce cyber risk management, we first need to define the term ‘risk’. Risk is the combination of the probability of an event and its consequence / impact. This is commonly denoted as:
Risk = Likelihood x Impact
Whereby, the likelihood of a cybersecurity incident is influenced by the presence of vulnerabilities within a (digital) asset and the active threat posed by potential actors seeking to exploit these vulnerabilities.
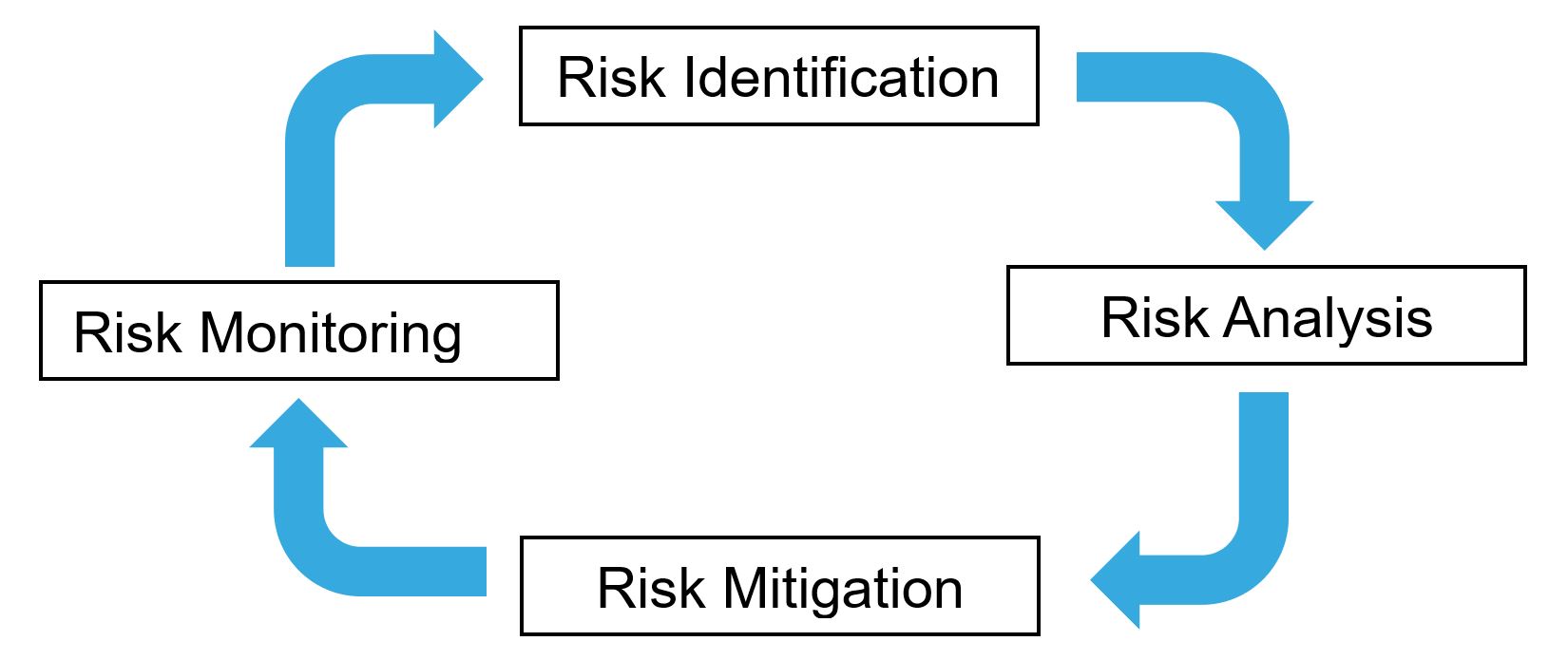
Risk management in cybersecurity is the continuous process of identifying an organization’s digital assets and the risks posed to them, reviewing already in place security measures, implementing solutions to mitigate security risks, and ultimately monitoring residual risk (see Figure 1).
Figure 1 Risk Management Process (source: Senthorus)
Step 1: Risk Identification
Every risk management process starts with the question what assets exist in the current environment, and what risks are posed to these assets. Several methods can be used to identify all possible risks, some of them are brainstorming sessions, usage of a risk matrix, maintenance of a risk register or an extensive SWOT-analysis (SWOT standing for strength, weaknesses, opportunities, and weaknesses).
Step 2: Risk Analysis
Once all possible risks are identified, the second step is to analyze these risks. For this purpose, two different methodologies can be used:
- Qualitative risk analysis: All risks will be ranked by their occurrence probability and impact severity, based on subjective judgement.
- Quantitative risk analysis: This assessment type serves to establish a financial evaluation of the risk’s impact.
Note: Assessing risks is often a very hard task. Firstly, there are many minor parameters with possible influence on the outcome. Secondly, it can be extremely difficult to translate these parameters into numerical values, for accurate calculations.
The risk analysis’ goal is to know which risks must be treated with highest priority as they could endanger an organization’s core business.
Step 3: Risk Mitigation
The results from the previous steps are then utilized to address the identified risks according to their priority. Several mitigation options exist:
- Avoidance: eliminate any exposure to a particular risk (e.g., completely avoiding public Wi-Fi-networks for company devices).
- Transfer: pass the responsibility to a third party (e.g., buying cybersecurity insurance).
- Reduction: mitigate the likelihood or severity of a potential risk by implementing proactive measures (e.g., deploying robust network security measures like a firewall, or a network intrusion detection system, also known as NIDS).
- Acceptance: acknowledging and embracing a certain level of risk without implementing any further mitigation controls (e.g., opting to not invest in any additional security measures due to cost-benefit considerations). The remaining risk is called: Residual Risk.
Step 4: Risk Monitoring
This step involves overseeing the continuous monitoring of the residual risk defined in step three (e.g., contracting, a third party to monitor the residual risk).
How the deployment of a SOC assists in the risk management process
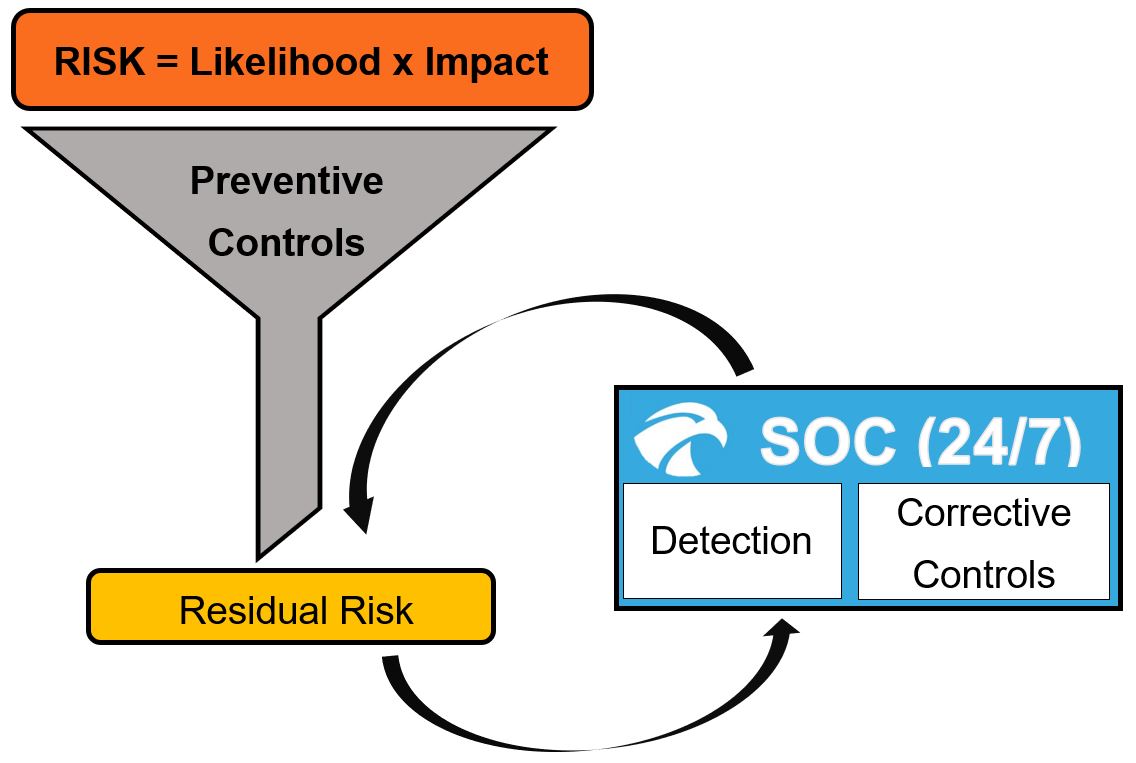
Deploying and running a SOC fortifies the risk management process not only through continuous monitoring of the residual risk, but also through the implementation of corrective controls.
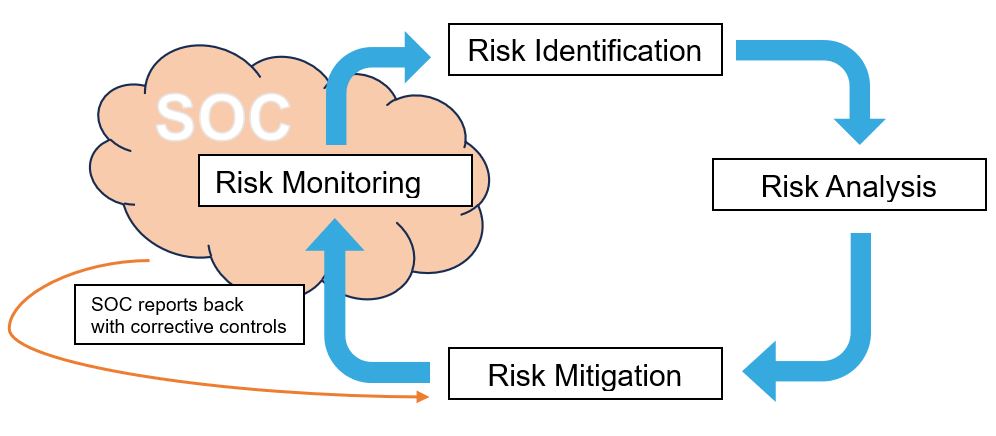
Figure 2 Integration of the SOC in the Risk Management Process (source: Senthorus)
Figure 3 Placement of the SOC within the risk management process (source: Senthorus)
Figure 2 and Figure 3 are a great illustration, showing where a SOC takes its position in the Risk Management process. Especially in Figure 3, we can highlight the ensured continuity of the risk management process by the SOC operations, specifically through the SOC’s reports on possible corrective controls.
The following points are the main objectives of a SOC:
- Address residual cyber risk.
- Help mitigating cyber risks.
- Improve the cybersecurity posture through continuous monitoring.
- Protect and defend an organization against rapid arising cyber threats.
- Strengthen the cyber-resilience of an organization.
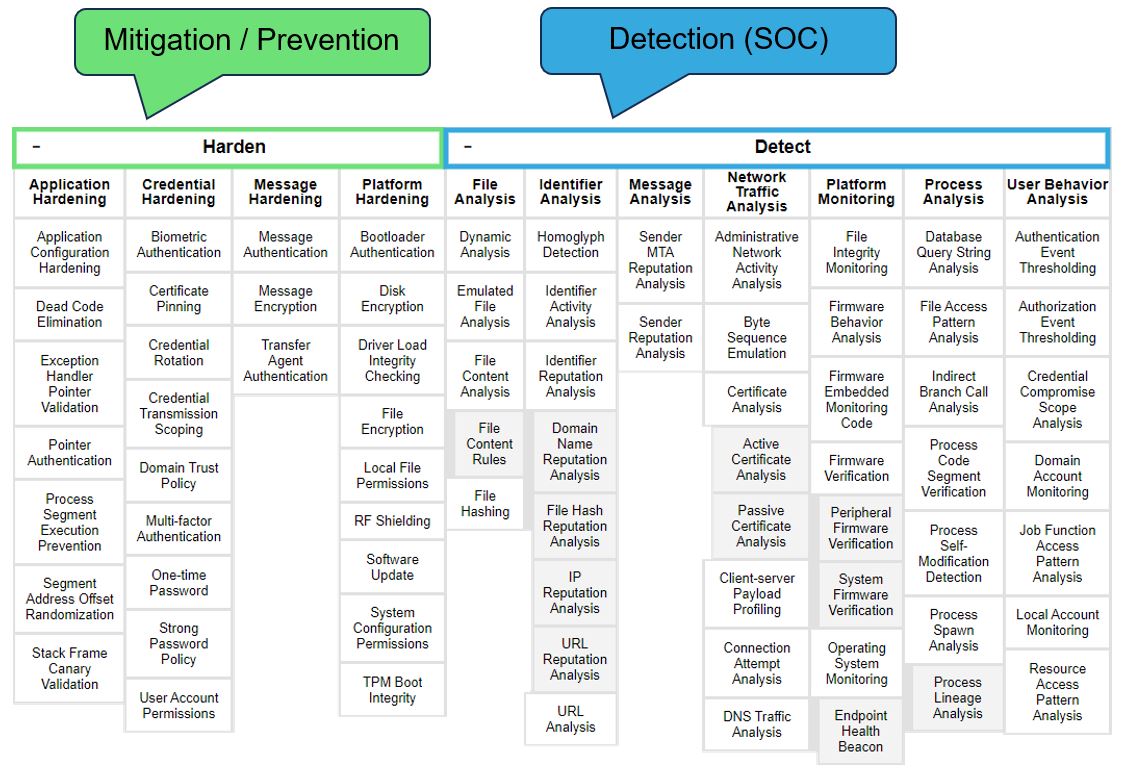
Figure 4 shows the separation of capabilities between the stages of mitigation / prevention and monitoring of the residual risk by the SOC. Senthorus’ detection capabilities are highlighted in blue, showing the wide range of detection capabilities offered. The most popular techniques used by Security Engineers to prevent security incidents are highlighted in green.
Figure 4 Mitigation and Detection capabilities in comparison (source: MITRE Defend)
Address residual risk with your SOC
Cyber risks should always be addressed first by implementing preventive controls as seen in Figure 4 highlighted in green. A SOC assists by addressing residual cyber risk, highlighted in blue in Figure 4. Optimizing the detection process is a main indicator of success for any SOC among handling alerts. This includes using Yara -, and SIGMA rules, or frameworks such as Alerting and Detection Strategy Framework (ADS) to reduce false positive alerts.
Detections can be further improved by the integration of cyber threat intelligence feeds, allowing for a proactive detection of evolving threats. Behavioral detections will help to identify unusual activities differing from a previously defined baseline.
Aggregation of low severity alerts into detections is a powerful way to detect advanced attacks. Some events may occur benign when considered in a small, specific scope. However, a succession of low severity events may indicate malicious behavior on an endpoint.
Benefits of deploying a SOC
Deploying a SOC has numerous benefits. We will address the most important ones briefly:
- Proactive Threat Detection: SOC teams continuously monitor network traffic, logs, and security events to detect potential threats before they can cause significant damage.
- Rapid Incident Response: With dedicated personnel and sophisticated tools, a SOC can quickly act on security incidents and this on a 24x7 basis.
- Enhanced Visibility: SOC activities provide comprehensive visibility into the security posture of an organization, allowing CISOs to take informed decisions to strengthen their security posture in preparation for future evolving threats.
- Compliance and Regulatory Alignments: SOC operations facilitate compliance with industry regulations and cybersecurity frameworks by ensuring the implementation of corrective security controls, data protection measures, and incident response procedures.
- Stakeholder Confidence: The establishment of a SOC demonstrates commitment to cybersecurity excellence driving confidence among stakeholders, customers, and partners, enhancing an organization’s reputation in the marketplace.
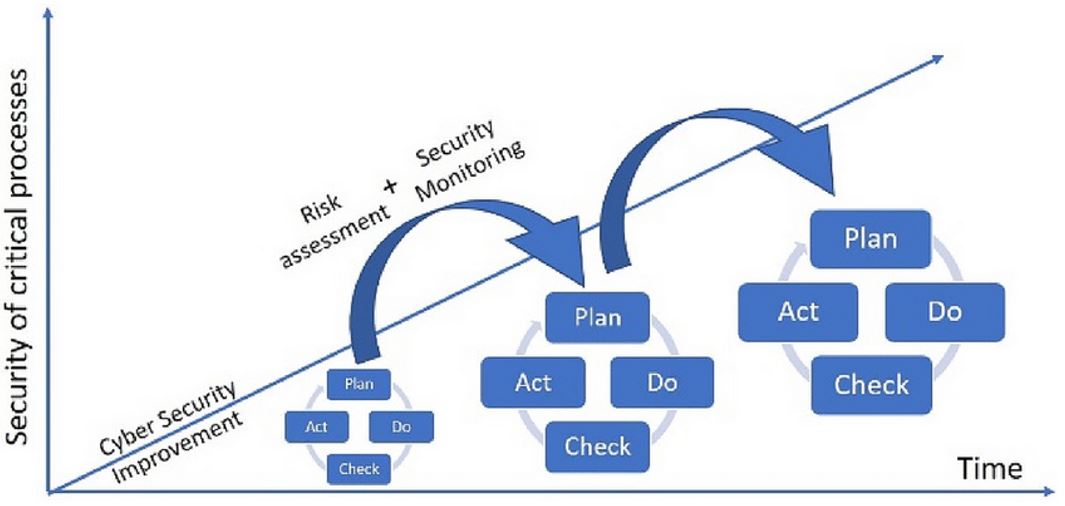
We can denote that all of the previous listed points contribute to the Continuous Improvement process of an organization (see Figure 5).
Figure 5 Continuous Improvement Process (source: ResearchGate)
Conclusion: Is deploying a SOC the missing puzzle piece?
In conclusion, the deployment of a Security Operations Center (SOC) represents a pivotal advancement in enhancing an organization's cyber risk management capabilities. Particularly, CISOs tasked with safeguarding critical assets and data, may find the deployment of a SOC an elegant solution to ensure the continuous improvement of their organization’s security posture. By centralizing threat detection, incident response, and proactive monitoring within a dedicated SOC environment, CISOs can gain invaluable insights into evolving cyber threats, allowing them to take the right measures before . With real-time threat intelligence, advanced analytics, and skilled cybersecurity professionals at their disposal, CISOs can effectively anticipate, detect, and neutralize cyber threats before they escalate, thereby fortifying an organization's resilience against a rapidly evolving threat landscape. The SOC not only serves as a proactive defense mechanism but also empowers CISOs to make well informed decisions, allocate resources efficiently, and align their organization’s security posture with business objectives, ultimately sustaining a culture of continuous improvement, hence staying one step ahead of threat actors.
In the second article of this series, we will take a closer look at the different deployment types of a SOC, presenting a comprehensive overview of their respective advantages and disadvantages.
The co-author

Ibrahima Diop
SOC Team Leader at Senthorus
A cybersecurity leader specializing in digital forensics, incident response, and training. With strategic prowess and relentless dedication, he safeguards against threats while empowering others in the realm of cyber defense.