Introduction
Energy infrastructures represent a critical concern for all cities and are increasingly the target of sophisticated attacks aimed at destabilizing certain countries. Particularly within the context of escalating geopolitical tensions. Attacks targeting electrical energy providers can trigger chain reactions leading to devastating consequences, particularly affecting safety and even causing natural disasters beyond their immediate impact on electricity availability.
These attacks are utilized as a veritable arsenal of war when motivated by geopolitical tensions. This was evident in 2022 in Ukraine when the attack on the electrical infrastructure was coupled with a physical military assault. Or more recently, between May 11th and 30th, 2023, a large-scale attack took place against Danish electrical actors, targeting up to 22 companies in the same campaign.
In this article, we will review these two attacks to draw concluding lessons regarding the tactics and techniques employed, along with recommendations to best monitor and protect critical infrastructures.
Ukraine 2022 – Sandworm APT manages to cut off electricity in multiple Ukrainian regions
This is not the first time Ukraine has been targeted by the APT Sandworm. We recall the year 2015 when they used the specific malware BlackEnergy3, followed by Industroyer/Crashoverride in 2016, successfully cutting off electricity for several hours, forcing operations to switch to manual mode to restore power.
On October 10, 2023, the APT Sandworm repeated its attack, this time with an even more stealthy approach and a more significant impact, using a new type of attack. The exact point of entry into the target infrastructure or the initial access date is not known precisely. However, it is known that the attackers were able to pivot to Supervisory control and data acquisition (SCADA) instances by exploiting the host hypervisor using an outdated version of the MicroSCADA software.
Sandworm used then a set of Living Off the Land Binaries (LOTL) scripts to directly impact the control of electricity stations by disconnecting them. LOTL refer to cyber criminals’ techniques leveraging non-malicious binaries, generally built-in operating system, to hide their malicious activities via legit processes.
The last phase of the attack involved the usage of a new version of CaddyWiper to erase attack traces on the IT side.
Tactics
The Mandiant incident response team estimates an intrusion around June 2022 (referring to Mandiant article), during which the attacker deployed a webshell Neo-REGEOARG on an internet-facing server, ensuring persistent access to the station's web servers. In July, this persistence was reinforced by deploying GOGETTER, an open-source tool acting as a tunnel to the attackers for their command-and-control servers over TLS.
Using SystemD, the adversaries managed to establish persistence for Gogetter's execution after machine reboots, all while disguising this service to appear legitimate.
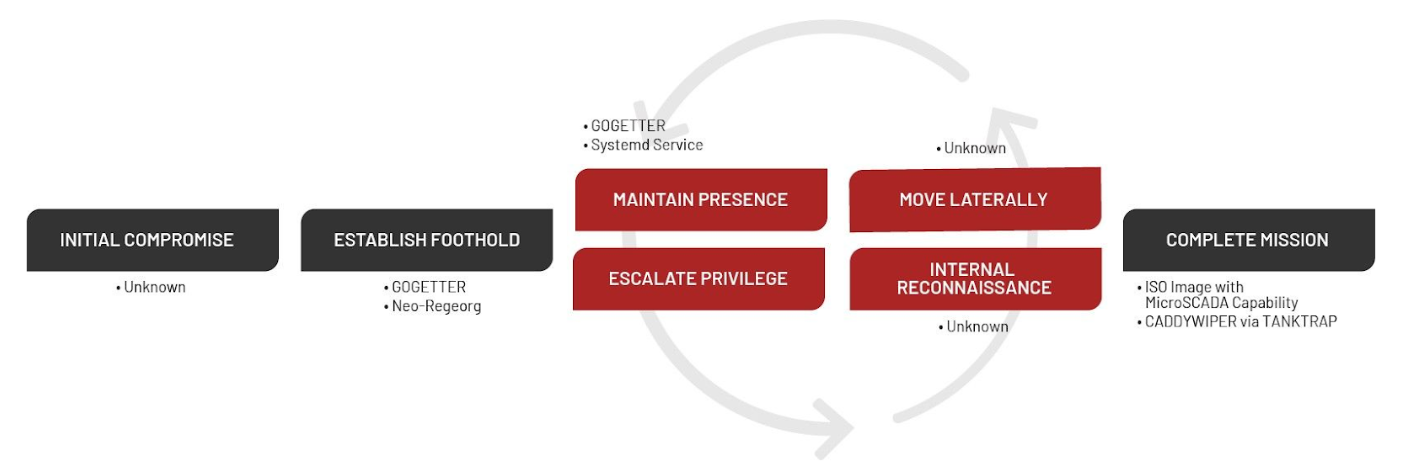
Figure 1 Incident targeted attack lifecycle - Source: Mandiant
By exploiting a vulnerability in this end-of-life version of the SCADA control system, they managed to insert an ISO containing three scripts (lun.vbs, n.bat, s1.txt). However, no obvious malicious payload was included in these files because they succeeded in translating their goal directly into the SCIL language, which is the scripting language for the MicroSCADA control system. These commands were then transmitted to the Remote Terminal Units (RTUs) of the substations, likely to open the circuit breakers and achieve the attack's objective.
By using the LOTL scripts, the attackers were able to remain discreet. To complete the operation, on October 12th, they deployed a new version of CaddyWipper via Group Policy Objects (GPO) and a scheduled task to clean up the traces left behind.
Denmark 2023 - Multiple attacks against energy sector companies
On May 11th, 2023, the Danish energy sector was heavily impacted by a series of targeted attacks, affecting no fewer than 22 companies involved in the energy domain. The group of attackers exploited a vulnerability (CVE-2023-28771) in Zyxel firewalls, officially known since April 25th, 2023. Zyxel is widely used in Denmark and is found in many critical OT infrastructures designed to protect against threats. Ironically, the attack vector was precisely the device meant to ensure the protection.
The attackers managed to leverage the resources of compromised entities in brute force and DDoS campaigns against other companies before the defense teams managed to isolate compromised infrastructures from the Internet.
Tactics
First wave
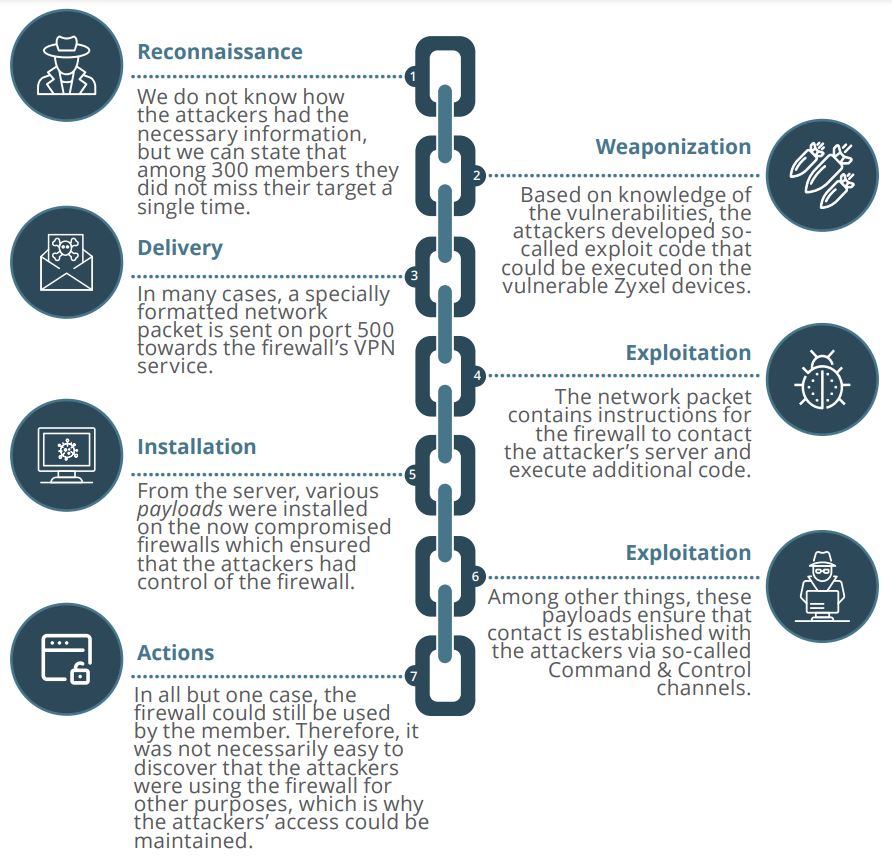
The vulnerability CVE-2023-28771 was exploited by sending a single crafted packet to port 500/UDP of the vulnerable firewall's VPN service. The attacking group conducted a deep reconnaissance, as all sent packets successfully reached their target without one miss. This indicates that they precisely knew which firewalls were vulnerable, even though this information was not available publicly on Shodan. As a result, the attacker could execute commands with root privileges directly on the device without authentication.
Once the attackers gained initial access, they proceed to the extraction of the vulnerable firewall configuration and user accounts information.
Second wave
On May 22nd, 2023, a second wave of attacks was observed, where compromised companies were seen downloading new software through insecure connections. Additionally, encrypted command and control traffic was detected, utilizing either a recently created domain or known malicious IPs associated with a variant of the Mirai botnet called Moobot. This time, it appeared that the attackers exploited zero-day vulnerabilities, which were disclosed by the Zyxel vendor two days after the beginning of the second wave attack.
Following the command-and-control activities, there was a coordinated DDoS attack on the United States and Hong Kong, as well as a SSH brute force attempt against a Canadian company, occurring just before the defensive containment measures.
Figure 2 Cyberkill chain of the attack - Source: Sektocert.dk
Recommendation
It is recommended to implement strict network segmentation between OT and IT zones, as well as critical zones within the OT network. Additionally, when aware of vulnerable assets and the unability to patch them, it is essential to segment them to minimize the attack surface while allowing production to continue. This is particularly crucial for End-of-Life products, as demonstrated by the success of the Sandworm attack.
Concerning operational industrial scripts and commands, collaborating with production teams is crucial to identify functions and commands for defining a configuration baseline. This helps to detect stealth techniques, such as LOTL. Effective collaboration within the industrial/production team would further enhance the ability to spot malicious activities, improving defense capabilities.
Log collection from EDR and centrally managed Antivirus systems to improve detection capabilities. Integration with a SIEM and enrich with Threat Intelligence feeds to detect attacks based on tactics and known IOCs associated with known botnets or APTs.
In addition to effective network segmentation, it is recommended to monitor potential threats to vulnerable systems using specific detection rules at the SOC level.
Monitor the OT network, paying particular attention to flows from IT to OT and OT to/from the internet. Establishing a 24/7 detection capabilities for swift response, utilizing passive monitoring solutions coupled with machine learning to detect any changes in your environment or abnormal connections.
If you have an interest in monitoring grid infrastructure, we invite you to download the Senthorus whitepaper by submitting the form below, which delves into the cybersecurity monitoring approach applied to the industrial sector, with a specific focus on advanced measurement infrastructure in the electric sector.