Introduction
As cybersecurity threats continue to evolve, attackers are increasingly leveraging sophisticated strategies aided by advanced technologies. One such approach involves the utilization of artificial intelligence (AI) to craft highly convincing social engineering attacks, including AI-powered phishing attacks and imitation of real users' behavior.
However, within a Security Operation Center (SOC), AI also plays a pivotal role in fortifying defenses and responding effectively to these evolving threats. At Senthorus, we harness AI-powered solutions like Microsoft Sentinel and Darktrace to bolster our clients' cybersecurity posture.
In this article, we delve into the dynamic landscape of AI usage within a SOC, examining innovative tools and future possibilities that empower SOC analysts to streamline workflows, accelerate incident response, and proactively adapt to emerging threats.
On the attacker's side
For an attacker, these tools can be extremely useful. They can use them for different sophisticated strategies.
One such approach involves the imitation of real users' behavior, where attackers leverage machine learning algorithms to create bots that mimic human interactions. That way they can more easily bypass traditional security measures.
Additionally, AI-powered phishing attacks have become more prevalent, with attackers leveraging data analysis and content generation algorithms to craft highly convincing and personalized phishing emails tailored to specific target groups.
Imitation of real users’ behavior
Attackers utilize bots that use machine learning algorithms to behave like real users. They train these models with data created by real people: keystrokes, mouse movements, browsing patterns, and more. That way, these bots can behave like humans. For instance, they realistically randomize the movement of the mouse when they click on webpage elements, and they make small mistakes when typing, just like a real user.
All these techniques add more difficulty to the detection of an attack. For example, hackers have the capability to scan a network or a web application discreetly, looking for exploitable vulnerabilities, while acting like genuine users. In other instances, cybercriminals were reported fraudulently boosting the number of clicks to gain a quick reputation on a malicious website.
AI-Powered Phishing Attacks
This kind of phishing attack uses machine learning algorithms to create very convincing and highly personalized phishing emails.
To generate these emails, attackers train the AI with victim data, often bought on the darknet. These datasets contain Open-Source Intelligence (OSINT) information about the victim (social media, enterprise website, …) and/or leaked data (emails, messages, …). With this dataset, the machine learning algorithm finds relationships between employees or customers, creating a uniquely tailored attack pattern for the victim.
In the last step, the AI generates custom content for the phishing email that, through its high specialization, is very hard to detect as malicious. Even though each email content is tailored for the designated victim, attackers can automate the above process, allowing them to operate on a large scale.
On the SOC Analyst side
In the dynamic realm of a SOC, the utilization of artificial intelligence (AI) has become integral to our daily operations at Senthorus. The usage of AI-powered solutions like Microsoft Sentinel and Darktrace allows us to fortify the security posture of our clients, at last establishing Senthorus as a true Next-Generation SOC. These advanced technologies enable us to detect and respond to threats with unprecedented speed and accuracy, enhancing our ability to safeguard critical assets and mitigate risks effectively.
In this section, we’ll first dive into two AI-powered tools that we use at Senthorus. Secondly, we will talk about possible future implementations of AI that could help us, and other SOCs, to automate incident response, accelerate investigations, and optimize detection capabilities.
Microsoft Sentinel AI-powered Anomaly Detection
At Senthorus, we leverage Microsoft Sentinel extensively across our client base, this close partnership with Microsoft was just recently fortified by them nominating Senthorus as one of the leaders for Swiss SOC.
In a security information and event management (SIEM) solution, AI, and machine learning are used to detect suspicious behavior in the organization of our clients.
A prominent example is Microsoft Sentinel which leverages machine-learning algorithms to detect anomalous behavior across several log sources. To do this, the algorithm is trained with various data like network traffic, user, and system logs. After this training, the algorithm establishes a baseline, any deviation from this baseline will trigger an alert. When an alert is raised, one of our analysts immediately investigates the activity of the device or user in question.
Darktrace Cyber AI Analyst
Darktrace is a cybersecurity company that uses artificial intelligence (AI) and machine learning to provide real-time threat detection, response, and prevention capabilities. Within this platform, there are several key components, designed to address different aspects of cybersecurity, and Cyber AI Analyst is one of them.
When the Darktrace immune system detects an anomaly, the Cyber AI Analyst automatically investigates those leads. It works with a huge dataset that grows every day by capturing investigation information. When a model breach occurs, the AI Analyst waits one hour to have sufficient evidence for the analysis, before starting an automatic investigation. The automatic investigation does not differ too much from the one a “classical” SOC analyst does. First, the AI analyst starts with a lead, and then forming a hypothesis, before checking the large dataset maintained by Darktrace for further information corresponding to the incident. In the end, the AI Analyst makes a conclusion and shows his work in the AI Analyst UI.
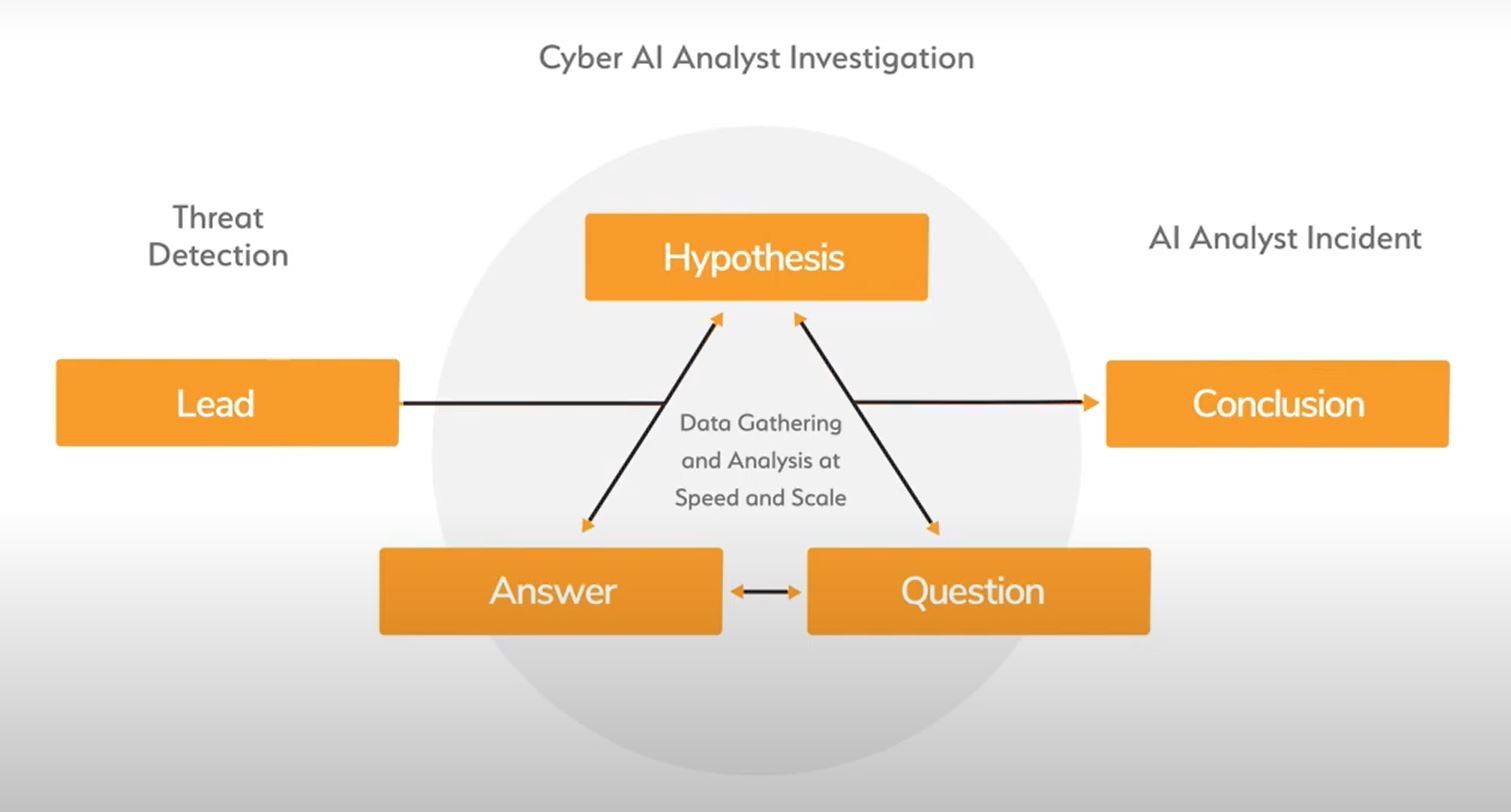
Source: « Cyber AI Analyst - The augmented security analyst | Darktrace » on YouTube.
Future possibilities
As SOCs continue to evolve in response to the ever-changing threat landscape, the integration of artificial intelligence (AI) holds immense promise for enhancing efficiency, effectiveness, and agility in cybersecurity operations.
By harnessing the power of AI, SOC analysts can enhance their workflows, accelerate incident response, and proactively adapt to emerging threats, while ushering in a new era of resilience and proactive defense in cybersecurity operations.
In the next sections, we are going to present three possible implementations of AI that can help SOC analysts further improve their workflows, accelerate incident response, and adapt proactively to emerging threats.
Automatic pre-filling of ticket
AI-driven automatic pre-filling of tickets promises to streamline incident response in SOCs. In this case, the AI model is trained with tickets previously completed by SOC analysts. Once the training is done an incoming alert will be analyzed and treated by the AI model, before closing the ticket a “four eyes check” with a human must be conducted. That way, tickets will still have the SOC’s personal touch.
AI models are able to automatically set the corresponding MITRE ATT&CK tactic and technique, rate the severity of the incident, and much more. This helps drastically save time and enables SOC analysts to focus on investigating and mitigating high-priority threats.
Investigation recommendation
When a SOC Analyst starts investigating a ticket, it often takes some time to find where to search for further information. Drawing historical data based on older tickets, AI algorithms can guide analysts through the entire investigation: which logs to examine, which tools to use, and so forth. This proactive assistance can speed up investigations significantly, enabling analysts to swiftly identify and mitigate security threats.
Rule tuning suggestion
This future implementation of AI can help SOC teams optimize their detection rules effectively, particularly in scenarios where a high volume of alerts is triggered by poorly defined rules. Leveraging AI algorithms, the system analyzes tickets written by SOC analysts to identify rules with a favorable true positive to false positive ratio. By prioritizing these rules for optimization or refinement, SOC analysts can significantly reduce alert fatigue, focusing their efforts on investigating genuine threats, and enhancing overall detection efficacy.
Conclusion
Throughout this article, we've delved into the crucial role of artificial intelligence (AI) from the vantage point of both attackers and defenders, with a particular focus on Security Operation Centers (SOCs). Attackers are increasingly leveraging AI-driven techniques, such as imitation of real users' behavior and AI-powered phishing attacks, to evade traditional security measures and orchestrate highly convincing attacks. However, SOC analysts have also powerful AI-driven tools at their disposal, enabling them to detect and respond to threats with unprecedented speed and accuracy.
Looking forward, the future of SOC operations lies in further leveraging AI, allowing SOCs to always stay ahead of the quickly changing threat landscape. Automated pre-filling of tickets, AI-driven investigation recommendations, and rule tuning suggestions represent promising avenues for enhancing SOC capabilities and staying ahead of evolving threats. As the cybersecurity landscape continues to evolve, the integration of AI will remain essential for resilience and proactive defense in SOC operations, ensuring organizations can effectively mitigate risks and safeguard their assets against ever-evolving cyber threats.
References
- https://darktrace.com/news/darktrace-cyber-ai-analyst-investigates-threats-at-machine-speed-4
- https://www.youtube.com/watch?v=Y0eLSRIFgFU&ab_channel=Darktrace
- https://www.youtube.com/watch?v=nqYJ1ReIdVU&ab_channel=Welcome.AI
- https://cyberaiworks.com/Cyber-AI-Analyst.asp
- https://learn.microsoft.com/en-us/azure/sentinel/anomalies-reference
- https://techcommunity.microsoft.com/t5/microsoft-sentinel-blog/microsoft-sentinel-customizable-machine-learning-based-anomalies/ba-p/3624436